T-Mobile accounts had been SIM-swapped on at least 104 occasions throughout 2022, according to Krebs on Security.
SIM-swapping refers to the unauthorized takeover of a mobile phone account, enabling access to information, including receiving text-based 2 Factor Authentication (2FA) codes. It involves hackers tricking the network provider into switching the account to a SIM under the hacker’s control.
“This means that stealing someone’s phone number often can let cybercriminals hijack the target’s entire digital life in short order — including access to any financial, email and social media accounts tied to that phone number.”
In December 2022, Nicholas Truglia was sentenced to 18 months in prison for stealing $23.8 million in crypto via SIM-swapping. The theft was related to a single victim named Michael Terpin.
Between January 2018 and December 2020, the FBI received 320 SIM-swap complaints. However, in 2021, this number skyrocketed to 1,611 incidents.
Over 100 T-Mobile accounts hacked
Security researchers focused on Telegram groups in which three distinctive hacker groups advertised access to T-Mobile customer accounts.
“KrebsOnSecurity is not naming those channels or groups here because they will simply migrate to more private servers if exposed publicly, and for now those servers remain a useful source of intelligence about their activities.”
Researchers logged the number of times a Telegram post announced T-Mobile account access to channel members.
Collating the data involved starting on Dec. 31, 2022, and counting backward, noting each time new access notifications were posted. But researchers abandoned the count by mid-May when 104 incidents were counted, leaving four and a half months of Telegram logs uncounted.
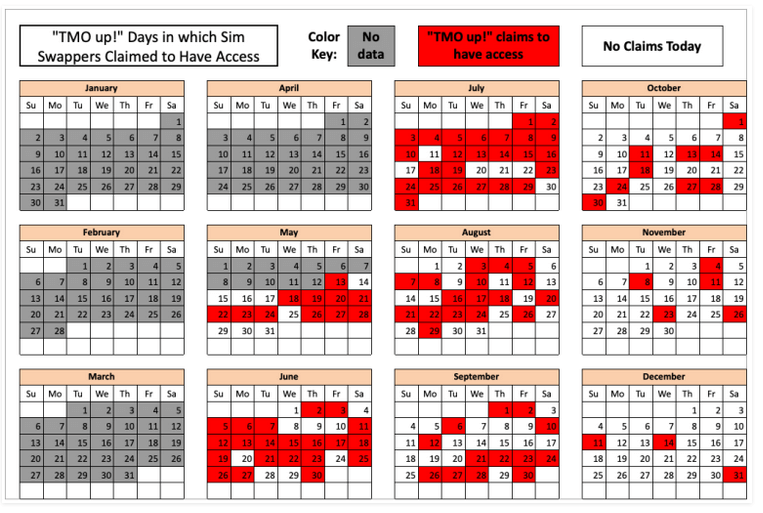
Considering the existence of other hacker groups, other Telegram channels, and other carriers, the 104 incidents noted is an under-representation of the scale of the problem.
SIM-swapping is an industry-wide
When approached for comment, T-Mobile said SIM swapping is an issue that affects the whole industry. The firm added that it is constantly fighting the problem, including improving the SIM-swapping process.
“We have continued to drive enhancements that further protect against unauthorized access, including enhancing multi-factor authentication controls, hardening environments, limiting access to data, apps or services, and more.”
The statement also mentioned incorporating intelligence-gathering operations, such as the one conducted by security researchers in this study.
Krebs on Security acknowledged that SIM-swapping is an industry-wide problem. However, they stated that rival carriers AT&T and Verizon featured less frequently in Telegram hacker groups.
In cases of these carriers featuring, hackers asked for between $2,000 and $3,000 for access, twice that of access to T-Mobile accounts – suggesting that T-Mobile SIM-swapping is easier.
Tips to counter SIM-swapping
Signs of a SIM-swap attack include the inability to call or text, login credentials for bank and crypto accounts no longer working, and unfamiliar transactions.
If encountered, the first action is to contact your network provider and request they lock down the account. Next is to contact banks and crypto exchanges to freeze your accounts.
Security firm Norton lists several methods of protection, such as awareness of phishing emails and sketchy links, having a strong phone account password, setting up an additional PIN with the phone carrier, use of authentication apps over SMS text authentication, and turning on transaction alerts.
The post Hackers access T-Mobile accounts more than 100 times in 2022: Tips to counter SIM-swapping appeared first on CryptoSlate.








